Malware Emails From Jerks
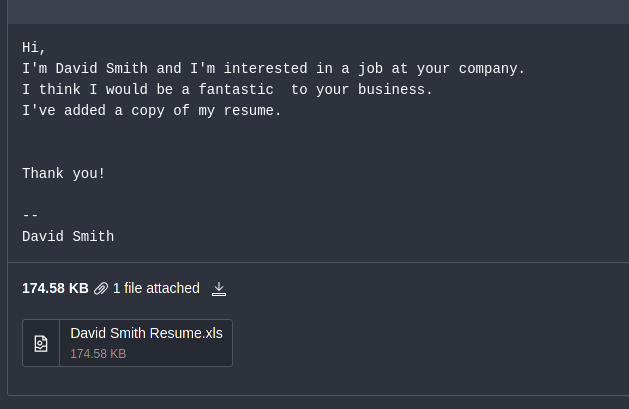
Today, I got an email inquiring about a job opportunity. This was immediately pretty funny, since I don’t employ anybody including myself. Even better, the guy sent a Microsoft Excel file as the ‘resume’, so even if I was hiring… Sorry bud, not going to be you.
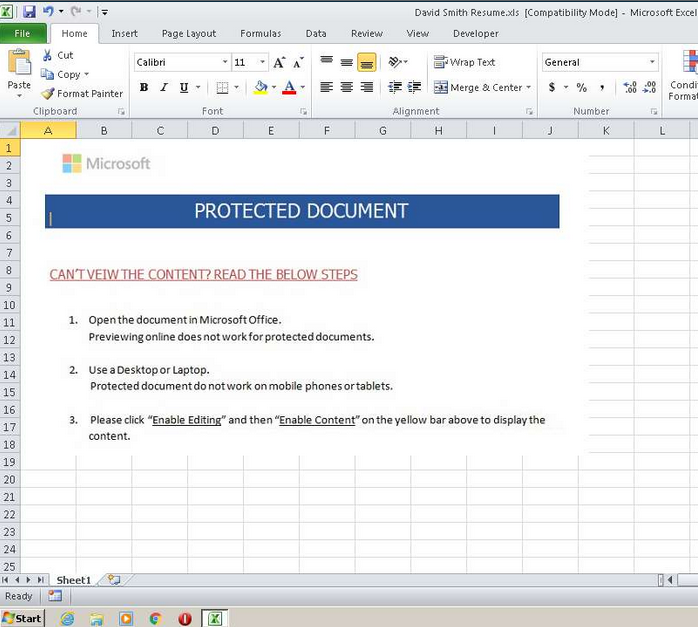
Now normally I just delete these documents and report spam. But seeing as how I’m locked into my house and have nothing better to do right now, I figured I might as well have some fun with this. So, here’s how to identify malware, and when you do, how to screw over the malware distributor.
Identifying Malware
First and foremost, this email attachment is a macro virus. This means that as soon as it opens in Microsoft Excel it will prompt the user to ‘Enable Macros’, then download a second stage trojan.
This loader then downloads additional malware to the system, typically ransomware.
So, the first step is to identify the threats. There are a few online tools for this, so we will start with the fastest and then move towards the most accurate.
VirusTotal
First step is to hit VirusTotal. It’s quick and dirty but gets the job done. In this case, this was the first time that VT had seen this hash, so very little recognition here.
https://www.virustotal.com/gui/file/006800b3ac96a69dc4e0797d89f3fb9211e8ec4da7e41737bfb51bc60ccaeb41/detection
CrowdStrike
Running Hybrid-Analysis generally gives a much better picture, since it runs a virtual machine that opens the file and runs whatever macros are inside it. Unlike VirusTotal, CrowdStrike finds lots and lots of nasties.
https://www.hybrid-analysis.com/sample/006800b3ac96a69dc4e0797d89f3fb9211e8ec4da7e41737bfb51bc60ccaeb41x
ANY.RUN
Any.run has a much more user-friendly viewport for these sorts of files, but doesn’t provide the same level of detail that CrowdStrike does. It does, however, show us a live view of the screen of our VM during this malware infection.
https://app.any.run/tasks/c11b50a6-202c-41d9-805f-fd7554e21651
…And it looks like David didn’t do a very good job on this one.
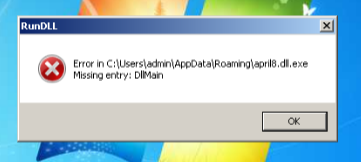
Analysis
So, what can we surmise from this sample? Well, it’s honestly pretty boring and pedestrian. Thanks for the crap malware, David.
This is typical Excel macro malware, likely a second stage downloader for some crypto locker that would show up after a couple hours to trash whatever network resources it can find.
Nasty Downloads
The macro downloads a file from a VM hosted in Alibaba Cloud, accessed by the URL http://march262020.com/files/april8.dll.
However, the malware also contains a few extra domains in case the main one gets taken down (which it will):
march262020.bestmarch262020.livemarch262020.network
There is also the domain that the email was sent from:
- jdscentral.com
And one other domain, though I’m not sure what this one is used for:
turn-eu.nenly.cn
Next, I like to check out whois data for the domain.
Domain name: march262020.com
Registry Domain ID: 2507617644_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.namecheap.com
Registrar URL: http://www.namecheap.com
Updated Date: 0001-01-01T00:00:00.00Z
Creation Date: 2020-03-26T16:11:03.00Z
Registrar Registration Expiration Date: 2021-03-26T16:11:03.00Z
Registrar: NAMECHEAP INC
Registrar IANA ID: 1068
Registrar Abuse Contact Email: abuse@namecheap.com
Registrar Abuse Contact Phone: +1.6613102107
Reseller: NAMECHEAP INC
Nasty Files
Once the trojan is installed, there are a few files that are executed:
| Filename | SHA1 |
|---|---|
| ieTneVi.dll | a7bdf8da3a30ac98a0df9fd0bd50f61a330056f1 |
| umzioxa.dll | a7bdf8da3a30ac98a0df9fd0bd50f61a330056f1 |
| april8_1_.dll | a7bdf8da3a30ac98a0df9fd0bd50f61a330056f1 |
Yep, all the dll’s it tries to load are exactly the same file with different names. Not sure what this is trying to accomplish, but our friend David could probably tell you.
The Server
So, what can we find out about the server hosting the second stage?
The second stage does earn a 13/77 on VT, so it is obviously malicious. But what is the actual server?
First step is to check out Whois. This IP address is registered to Alibaba Cloud (Germany).
NetRange: 47.254.128.0 - 47.254.191.255
CIDR: 47.254.128.0/18
NetName: ALICLOUD-GM
NetHandle: NET-47-254-128-0-1
Parent: AL-3 (NET-47-250-0-0-1)
NetType: Reassigned
OriginAS: AS45102
Customer: AliCloud (Germany) GmbH (C06869651)
RegDate: 2018-01-09
Updated: 2018-01-09
Unfortunately, shodan hasn’t scanned this box yet, so we’re on our own here. Running a curl -vvv 47.254.169.119 gives us this view of the headers:
> GET /files/april8.dll HTTP/1.1
> Host: march262020.com
> User-Agent: curl/7.68.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Server: nginx
< Date: Fri, 10 Apr 2020 02:22:43 GMT
< Content-Type: application/x-msdos-program
< Content-Length: 372736
< Connection: keep-alive
< Last-Modified: Thu, 09 Apr 2020 17:43:47 GMT
< ETag: "5b000-5a2df28a71ac0"
< Accept-Ranges: bytes
Neat, so the server is on Nginx. Good choice, David. What else are you hiding?
According to nmap, a bog standard Buster box.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 c9:c1:13:91:22:45:ad:cf:63:99:53:d0:bc:e9:84:4e (RSA)
|_ 256 78:be:ba:6f:b4:54:6b:c0:7c:44:3d:6c:8a:69:59:df (ECDSA)
80/tcp open http nginx
|_http-title: 403 Forbidden
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Taking out the Trash
So at this point I think it’s safe to say that David’s up to no good.
As of tonight, the 9th of April, I have submitted abuse reports:
- To NameCheap for the march262020.* domain
- To Alibaba Cloud for the server used to distribute malware
- To NameCheap for the jdscentral.com domain
What can be learned?
For those of us who use the web with integrity, it’s quite simple, don’t open strange emails from strangers.
But there’s a lot more to learn for spammers. This was a pretty botched execution. David, you need to do better.
- Do your research. It’s pretty obvious from my About page that I have no interest in hiring people.
- Be more selective with your target and adjust your methods accordingly. Again, a cursory glance at public information about me that I exclusively use GNU/Linux desktops, so what use would a Win32 binary be? Absolutely useless, David.
- Who on earth sends their resume as a spreadsheet? Has this phish ever worked? Ever?
Either way, the domains will be coming down very soon. One less scumbag out there 😄