Stop Putting Your SSH Keys on Github!
Hot take:
Stop putting your ssh keys on GitHub!!!
For that matter, stop putting your keys in any kind of repository. Seriously, your private keys are private for a reason.
Okay, let’s back up a little here. This morning some articles made their rounds about Cisco distributing network device firmware with keys and certs embedded in them. Now that happens all the time (ugh) but in this particular case, they were the keys of presumably a Huawei employee. Now if you’ve been following the news, you’ll know that looks bad. Heck, even if you don’t it’s not a good look for them.
But it’s okay because they’re SG series devices and nobody cares.
Regardless, after some more thorough inspection it was found to be originating in an open source framework that Cisco leverages in their build process or firmware.
Not the first time, not the last time
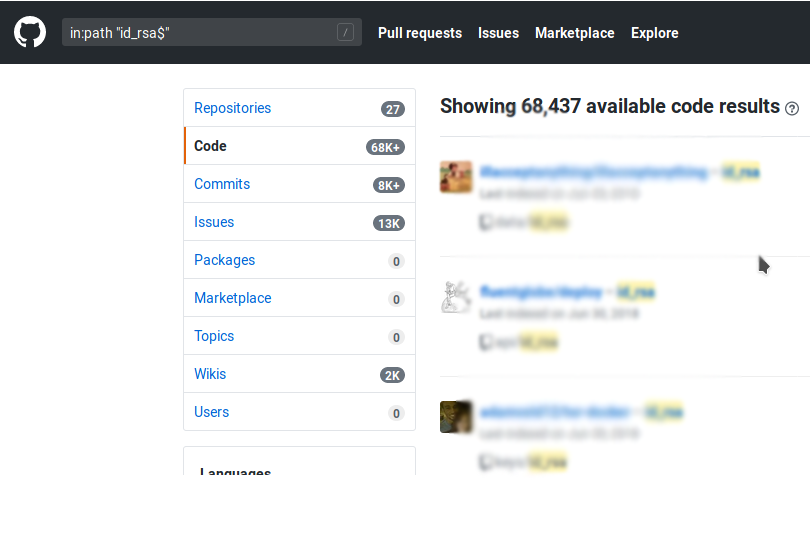
Truly, this is indicative of a much larger problem in the industry and community. Putting your keys in git is easy and feels good.
In fact, it’s so good that tens of thousands of GitHub users have done just this. Sure, most of these projects are small and only have a few users if any at all, but the odd time we see keys making it into projects with widespread use.
Just going through the search results on GitHub, the most common reason people are committing their keys seems to be to make code deploys and site updates easier and more portable. However, as we see this is not a great idea. Anybody that stumbles across your public repository can quickly and easily gain full access to your website or app. Once they’re in there it’s hard to say what kind of bad things will happen. If they’re nice, they’ll patch last month’s CVEs… If they’re not nice they might add CoinHive to your homepage and cook all your visitors' CPUs to make a couple bucks, or worse, deface your site in a humiliating way.
What you should do instead
First and foremost, don’t ever commit your private keys or move them into a directory that you use for change control. Generally, it’s a good idea to keep them in ~/.ssh if you can.
Next, include rsa keys in your .gitignore file to prevent them for accidentally being added to a commit. Here’s an example:
id_rsa.pub
id_rsa
id_dsa.pub
id_dsa
*.pem
*.key
That should exclude most ssh keys and certificate private keys from being added to your repo.
And finally, just configure ssh correctly. Most of the reasons to abuse git can be eliminated by configuring your own ssh client. For example, if you want to use a different keypair for dev and prod here’s one way to do that:
~/.ssh/config
Host prod-server
HostName www-prod.fakedomain.net
Port 22000
User foobar
IdentityFile ~/.ssh/prod-server.key
Host dev-server
HostName www-dev.fakedomain.internal
Port 22
user foobar
IdentityFile ~/.ssh/dev-server.key
And just like that, SSH as well as tools like SFTP and Rsync will use the correct remote access configuration, eliminating the need to store your keys with the projects they’re used in.
So please, whether you’re on team Cisco or Huawei, please take appropriate measure to keep your keys off GitHub!